What Does Alpha Mean In Passwords
I you are not at least 18 years of age or the age of majority in each and every jurisdiction in which you will or may view the Sexually Explicit Material whichever is higher the Age of Majority ii such material offends you or. Update the docstring of the type built-in.

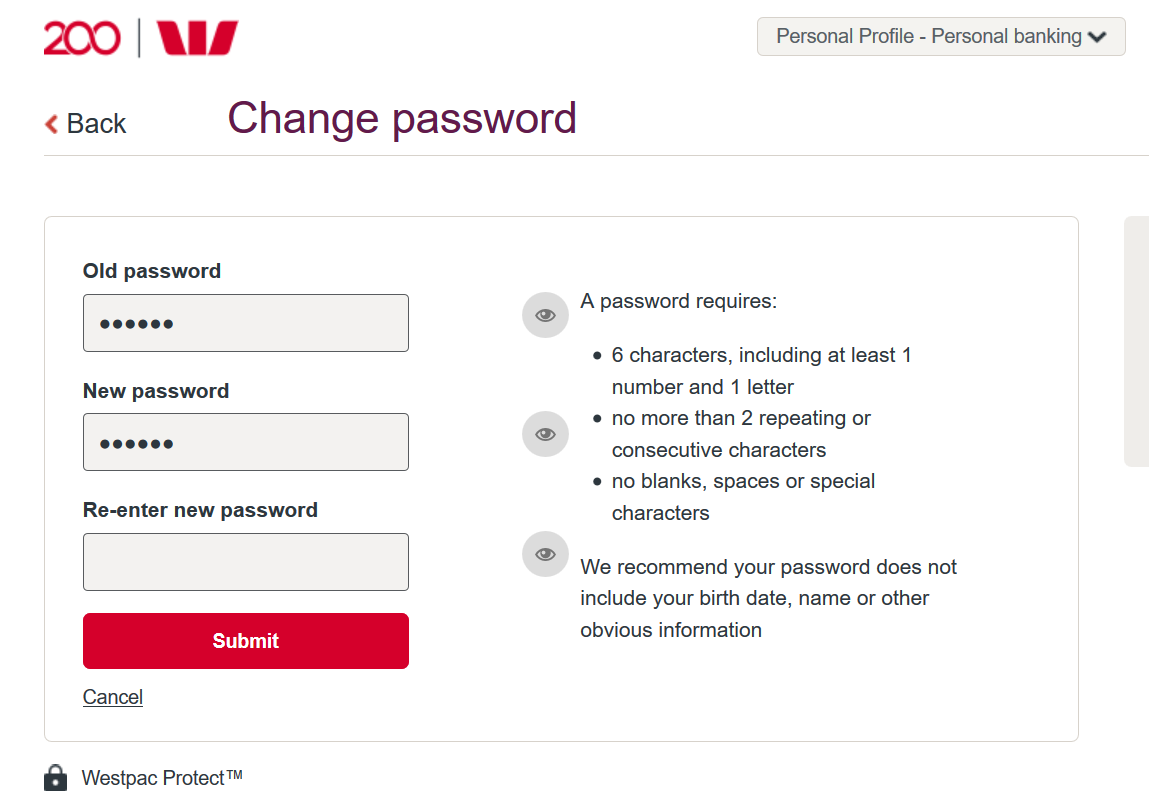
Password Policy Enforcer Character Rules
Hackers can monitor internet packets on WiFi and decrypt SSL to steal your passwords.

What does alpha mean in passwords. But while the breadth of earthly biodiversity may be well known the incredible things our animal counterparts can do are often hidden to humans. Working Copy Upgrades WARNING. Welcome to Access Online.
This website contains information links images and videos of sexually explicit material collectively the Sexually Explicit Material. That username is already taken. The case described earlier for the paired t-test or the Wilcoxon signed-rank test is the simplest form of a repeated measures designThe use of multiple comparisons with repeated measures is very common especially in studies evaluating the time course of an effect.
Usernames should only contain letters numbers dots dashes or underscores. Passwords do not match. The ROM Hacks Studio once known as our Hacks Showcase is the best place on the web to find ROM hacks.
Socketsocket documentation is corrected to a class from a function. Marino in Research in the Biomedical Sciences 2018 365 Multiple Comparisons with Repeated Measures. It can mean sir master owner or even refer to an idol.
This is the divine name for God. Generate a hard to guess easy to remember password. With an estimated 777 million species of animals on the planet the animal kingdom is an undeniably diverse place.
Alpha numeric is a classic. Please provide a valid first name. As Jonathon Reinhart commented youre seeing the effect of merges.
As the documentation you quoted mentions it also implies --single-branch which simplifies talking about thisThe important point here is that the walk visits all parents of each commit whichfor each depth levelis more than one. Link doc for sysprefix to sysconfig doc on installation paths. SetInterval Random Number.
The University of North Alabama is an accredited comprehensive regional state university in alabama offering undergraduate and graduate degree programs. Upgrade to Inside PRO risk-free for 30 days. This is the consistent truth of Scripture - Jesus is Yahweh or Jehovah.
Join Inside PRO to gain access to our Slack community of over 2500 entrepreneurs and executives participate in community-only AMAs and more for only 200 per year - try risk free for 30 days. Properly marked-up grammar tokens in the documentation are now clickable and take you to the definition of a given piece of grammarPatch by Arthur Milchior. The --depth parameter refers to how deep Git goes on a walk from each starting point.
If you are using several versions of Subversion on your machine be careful about which version you use in which working copy to avoid accidentally upgrading a working copy. Browse our curated collection. However on a number of occasions it is the Greek equivalent to the Hebrew word Yahweh or Jehovah.
Do NOT continue if. How to make this server process run forever. If a Subversion 16 client encounters a pre-16 working copy it will automatically upgrade the working copy format as soon as it touches it making it unreadable by older Subversion clients.
Passwords should have at least 6 characters. In the end the output of all functions is just binary digits which are usually represented and stored either as the hex representation or as the base64 representation. Upper and lower case letters with a few numbers thrown in for good measure.
If your wifi is public can you change your wi-fi to private and have password on it Public WiFi hotspots are insecure and prone to hacking attempts. What does the d flag mean in a javascript RegExdone is not supported in ajax callback. How to handle an iPhone alert with 2 buttons want to click the non default button CakePHP recursive delete.
Jesus Christ is designated as the Lord in many New Testament references. How to pass a callback function to a StreamController. Please enter your information to log in.
Passwords are usually not encrypted they are hashed and usually represented inthe form the function outputs them - so you can find many of those forms in the links above.

How To Brute Force A Password Protected Rar Zip File Using John The Ripper Hacking Dream Art Logo Passwords Force

Good Passwords Via Asciiartist Com Don T Worry Too Much About Hackers Cracking Your Password Just Make Your Ascii Art A Ascii Art Text Tutorial Funny Texts

Fix Password Must Be At Least 6 Characters One Special Characters One Upper Case Youtube

How Does Freemasonry Make Good Men Better Masonicfind Freemasonry Freemason Rosicrucian

Character Password An Overview Sciencedirect Topics

Character Password An Overview Sciencedirect Topics

New Password And Username Policies Sapien Blog

How To Reset Your Password Loom

The 8 Character Password Is Dead Technology Insights Blog
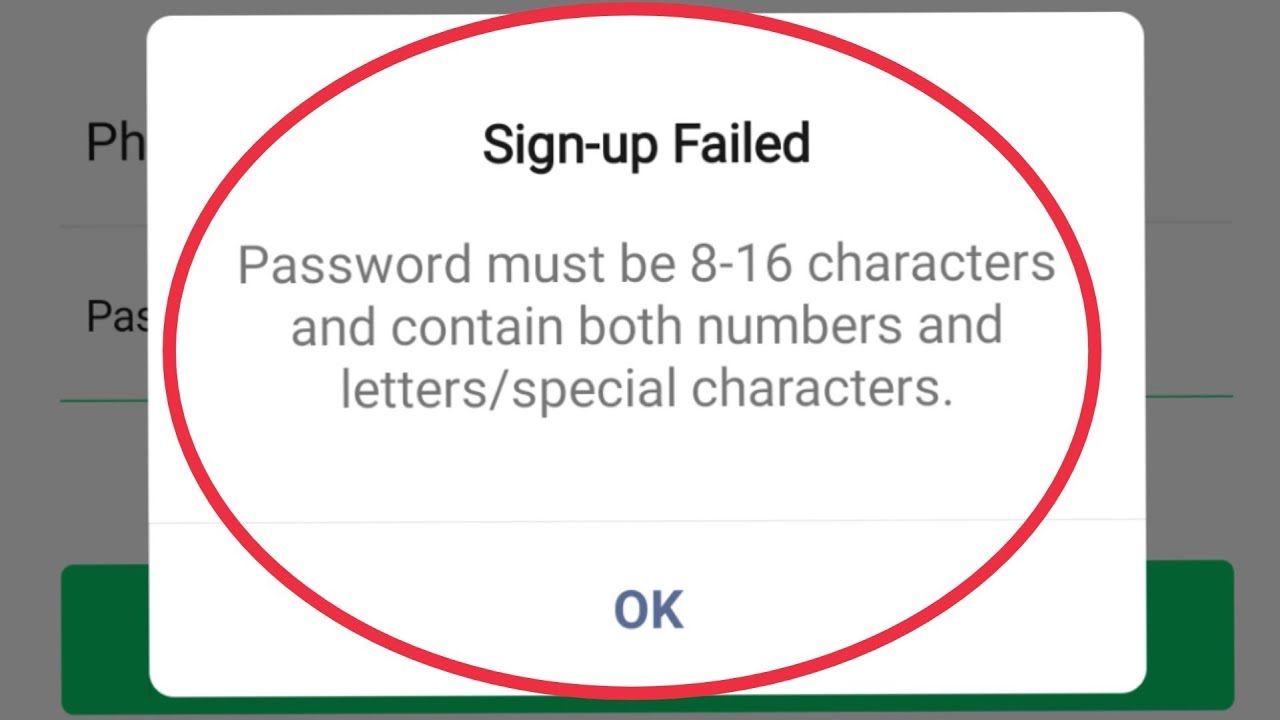
Wechat Password Must Be 8 16 Characters And Contain Both Numbers And Letters Social Character Youtube

Enforcing Complex Passwords At The Site Level

6 Password Tips To Protect Against Business And Identity Theft Comtech Computer Services Inc
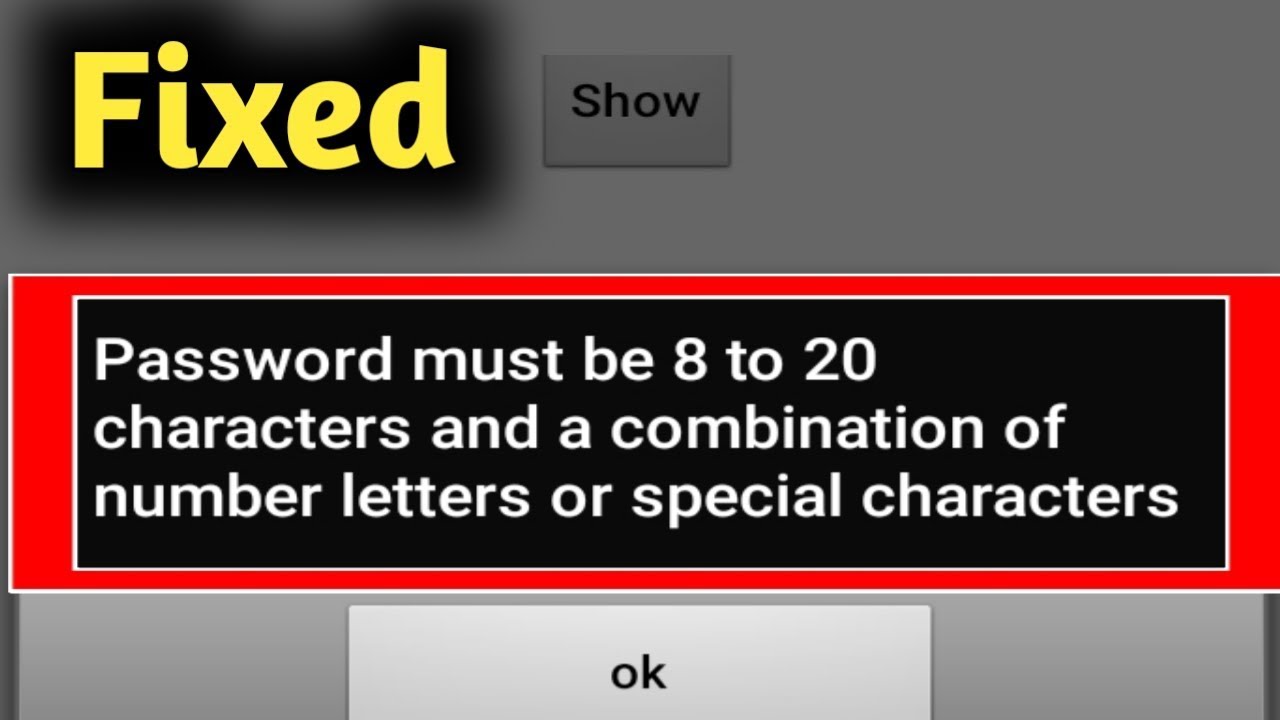
Fix Password Must Be 8 To 20 Characters And A Combination Of Numbers Letters Or Special Characters Youtube
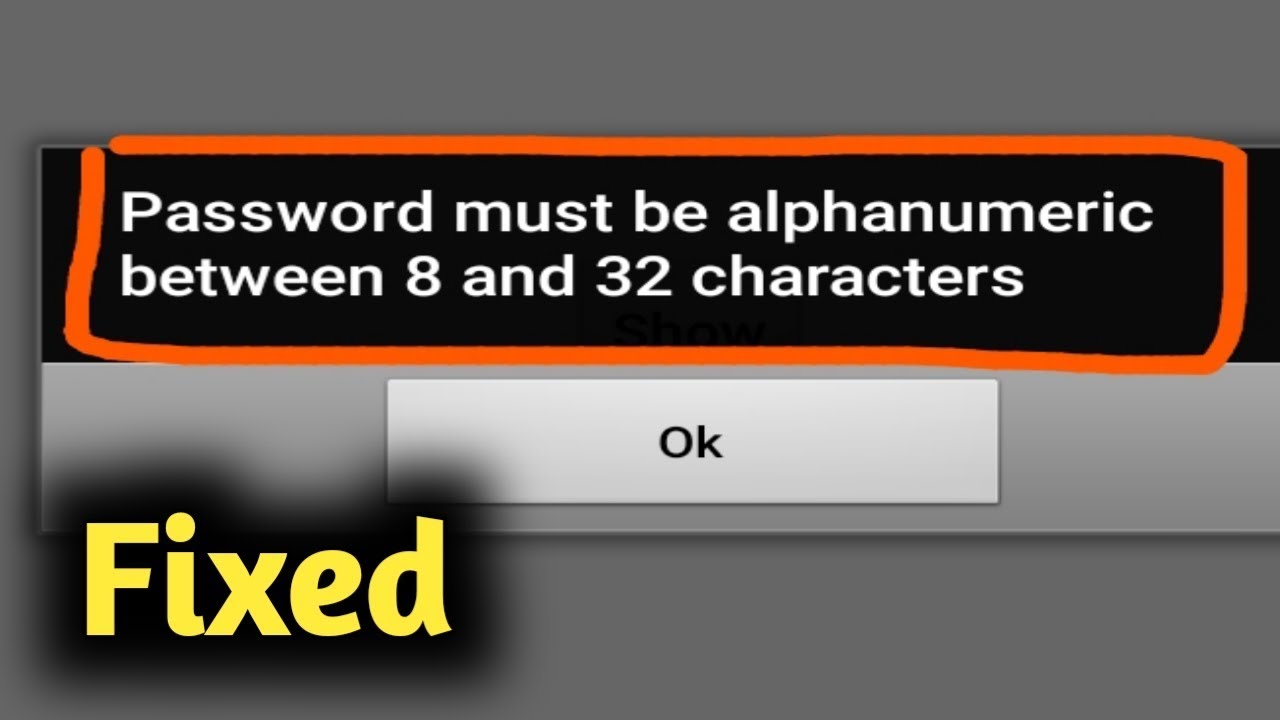
Fix Password Must Be Alphanumeric Between 8 And 32 Characters Youtube
4 Tips For Creating Secure Passwords The Mac Security Blog

Common Assessment Tool Cheatsheets Assessment Tools Computer Science Programming Cheating